Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
E-Fraud Prevention Based on the Self-Authentication of E- Documents based on Improved Particle Swarm Optimization (IPSO) Algorithm and Support Vector Machine (SVM) Techniques
Authors: Utkarsha Kulkarni , Rahul Paikrao
DOI Link: https://doi.org/10.22214/ijraset.2024.65243
Certificate: View Certificate
Abstract
Fraud is an intentionally deceptive action designed to provide the perpetrator with an unlawful gain or deny a victim a right. Fraud activities can be carried out by individuals, multiple individuals, or a business firm. This research aims to construct a deep convolutional neural network model to detect anomalies from regular patterns produced by competitive swarm optimization, with a strong focus and emphasis on fraud scenarios that cannot be detected using prior records or supervised learning. This algorithm classifies the fraud activity using real-time and another available dataset compared with the existing algorithms.
Introduction
I. INTRODUCTION
The current state of traditional commerce is changing in response to virtual businesses and the Internet. E-commerce has greater value now that there is a worldwide market, more freedom, and more competition and everything is dependent on e-commerce as it also makes it simpler and more accessible to innovate in the payment and banking sectors making life simple for users, whether they are consumers or business owners or even individuals. It is important in the more competitive global economy as nowadays people are moving away from conventional markets and toward the growing global market. It has a variety of restrictions in addition to providing customers with conveniences but as per the day-to-day businesses and trades online payment is essential.
The requirement for the financial and banking sectors has grown immensely as the size of the global market has expanded along with the increasing economy. With the use of connected phones like a laptop, mobile phone, desktop, PDA, etc., online payments enable you to make transactions from any place and anytime and this results in the elimination of traditional commerce’s constraints are the primary driver of the expansion of electronic payments. The user may physically visit the bank to complete the transaction without having to wait for a very simple and important task. It offers several advantages such as speedier transactions along with ease that may be completed in a matter of minutes.
There are two methods of execution of both online and offline electronic payments in various environments. Virtual payment may be recognized as payment processing or online payments. Account owner’s sensitive details are needed for online payments it might consist of some card and bank account details along with individual’s details. Physical payments can be identified as offline payments that are usually carried in banks where the account holder needs to be present along with his bank details. These frauds can be carried out in a variety of ways. Credit - card fraud is frequently committed using techniques including phishing, identity theft, skimming, using lost or stolen cards, card cloning, etc. In addition to these techniques, other mechanisms enable credit card frauds, such as malware or keyloggers that can steal credit card information during an online transaction, or scanners which are used to read your credit card information. While online payment does not require the signature or PIN of your card, it makes the process easier. Most of the websites are stealing card details and selling them to third parties, a number of the fraudsters are available on the dark web so difficult to trap. There are various payment mechanisms available on the market for online payment.
In the modern day, online banking has become the most popular service used by all users. Banks collect vast amounts of useful information on their customers and their transactions every second.
Financial institutions cannot gain the insights they need without first securing and properly analyzing this important data utilizing big data analytic methods. The current business climate places a premium on analysing massive data sets consisting of diverse data to unearth previously unseen patterns, market trends, client preferences, and other business insights. The purpose of this research is to suggest a strategy for executing IPSO-SVM to detect and prevent financial fraud in the digital world. This investigation introduces an improved particle swarm optimization of support vector machine technique model for fraud detection by combining optimized particle swarm optimization (IPSO) and support vector machine (SVM). The proposed approach outperforms other traditional models or algorithms.
II. EXISTING APPROACH
The Deep Neural Network is one of the most advanced artificial intelligence techniques for solving computer vision issues. The Deep CNN, a feed-forward neural network model, belonged to the deep learning class and was employed in several agricultural image classification projects. Filters are used by the convolutional layer, which is effective for Deep CNN, to extract information from the input images. The performance of Deep CNN can only be improved with a huge number of training instances. Reducing the need for feature engineering is one of the main advantages of utilizing Deep CNN for photo categorization. Each of the many layers that make up Deep CNN has several convolutions. In the earliest, more comprehensive layers, they generate a variety of interpretations of the training samples, progressing up.
In arrange to supply more discriminative highlights, the convolutional layers extricate numerous lower-level characteristics. The convolution layer is too principal part of Profound CNN. Include building, a particular conduct perspective of profound learning, speaks to a critical headway over standard machine learning. The down-sampling strategy is carried out along the spatial by the pooling layer. It advances by having few parameter choices. The max pooling approach was utilized within the convolution layers of the proposed models. Max pooling accomplishes way better than normal pooling within the proposed Profound Classification calculation. Dropout may be a significant layer that clarifies evacuating objects from the arrange. It is an overfitting diminishment regularization approach. With dropout values extending from 0.2 to 0.8, the proposed show was prepared and compared. Utilizing the results from the convolutional and pooling layers, the thick layer at that point conducts the classification.
Profound CNN could be an exceptionally iterative handle, and to induce the ideal demonstration, numerous models must be prepared. Slope plunge may be a principal optimization approach that executes the angle steps while utilizing all preparing illustrations for each arrangement. It is additionally known as group slope plummet. Slope plunge is challenging to achieve with an expansive preparation set.
III. PROPOSED APPROACH
The suggested approach is a novel mix of the deep learning techniques CSO and DCNN (in which CSO is used for feature selection and DCNN is used for classification) for identifying financial fraud. In the other approaches, the hybrid feature selection and classification strategy yields successful results.
A. Feature Selection
The huge optimization model is solved by skilled competitive swarm optimization (CSO), and learning is derived from the chosen competitors. Each iteration dynamically splits the population's particles into two sections, and bilateral competition is created between the particles in each group [21, 22]. the beginning of a G particle in a space of N dimensions. By confirming the fitness value, the fitness function assesses the qualities and yields the largest possible replies. The terms are selected at random for the fitness function computation, and a workable solution is produced for the terms that were selected at random. Equation estimates the MAD value as follows:
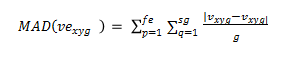
The values in the loser will cause the velocity and position to be adjusted, producing a new position. The function value of the newly formed swarms is calculated using equation (1), and the winner receives the swarm with the highest fitness. Dispersion, which happens immediately after a given generation and would be a serious disadvantage for the CSO, will arise because of the new selection swarms. The benefit of the suggested approach is that it provides a high degree of accuracy, enables one to retrieve additional time and assess the precision, and reduces credit fraud.
Where fe denotes the number of the feature, g denotes the reviews retrieved from the user tweet, ???????????????????? denotes the result of the swarm intelligence path vector, and sg denotes the number of the segmented group containing x features. The primary goal of employing MAD as a fitness function is to determine the score of each part as well as the distance between them. In the region of search, the solution value chooses the fitness value with the highest MAD.
Algorithm 1
Proposed CSO for feature selection

B. Classification Using A Deep Convolutional Neural Network
Deep Convolutional Neural Network (DCNN) using Rectified Linear Unit (ReLu) as a learning rate is used to help classify the best features. The feature extraction and classification phases make up DCNN. Convolution and pooling layers are included in the feature learning step. The fully connected and SoftMax layers are present during the classification step. The learning of picture features is facilitated by the Deep CNN, and categorization is straightforward.
- Convolution Layer: The aggregate of the output from this layer’s multiple filters as they pass over the data input is done using the component-by-component multiplication approach.
- The result of this layer is then calculated as the input’s responsive rate.
- Pooling Layer: The output dimensionality is decreased by the pooling layer, and the most well-known max pooling technique is used to display the maximum pooling filter value. Max pooling is a workable method that significantly minimizes the size of the input sample [23]. The summation and merging procedures are accomplished via the maximum pooling methodology. Fully Connected Layer: The convolutional layer result reveals that this layer integrates non-linear data from high-range properties. This layer learns the non-linear functionality in that region.
- SoftMax Layer: This stage involves categorization, and the output units—a normalized exponential quantity of output data—use the softmax function. This denotes that the output frequency and functionality are distinct. In addition, the progressive pixel value improves the likelihood to the highest degree possible.
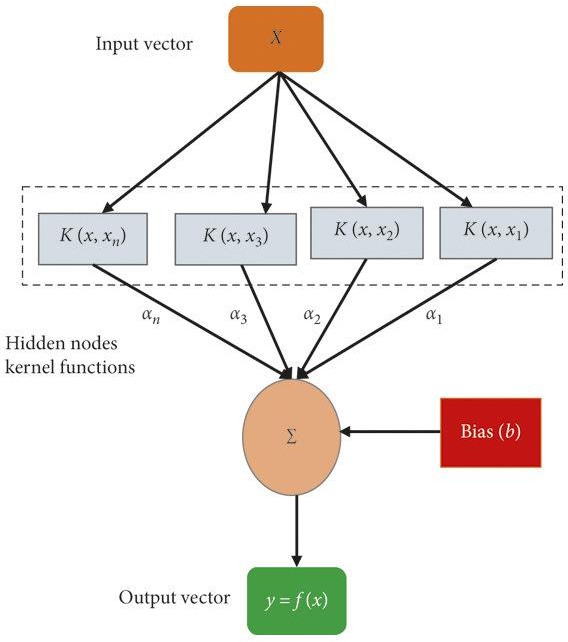
IV. SUPPORT VECTOR MACHINE ALGORITHM
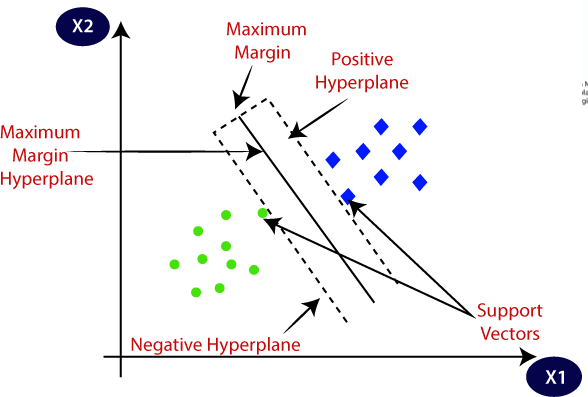
Support Vector Machine or SVM is one of the most popular Supervised Learning algorithms, which is used for Classification as well as Regression problems. However, primarily, it is used for Classification problems in Machine Learning.
The goal of the SVM algorithm is to create the best line or decision boundary that can segregate n-dimensional space into classes so that we can easily put the new data point in the correct category in the future. This best decision boundary is called a hyperplane.
Conclusion
In summary, since online payments just require the user credentials from the credit card to complete an application and then charge money, they are important in today\'s worldwide computer environment. Therefore, it\'s important to design the optimal strategy for identifying the maximum amount of online system fraud. Accuracy, MAE, and MSE are used to examine how well the suggested and current approaches work. The performance result shows how effective the suggested strategy is, and it works better than the current methods. Compared to current methods, such as CNN, the suggested strategy gets the maximum accuracy for three data sets. The greatest accuracy was attained, indicating that the recommended approach is effective in identifying cyberattacks. Compared to current methods, the suggested methodology has a very low error rate.
References
[1] A. Abdallah, M.A. Maarof, A. Zainal, Fraud detection system: a survey, J. Netw. Comput. Appl. 68 (2016) 90–113. [2] J. West, M. Bhattacharya, Intelligent financial fraud detection: a comprehensive review, Comput. Secure. 57 (2016) 47–66. [3] V. Van Vlasselaer, T. Eliassi-Rad, L. Akoglu, M. Snoeck, B. Baesens, Gotcha! Network-based fraud detection for social security fraud, Manag. Sci. 63 (9) (2017) 3090–3110. [4] J.O. Awoyemi, A.O. Adetunmbi, S.A. Oluwadare, Credit card fraud detection using machine learning techniques: a comparative analysis, in 2017 International Conference on Computing Networking and Informatics (ICCNI), IEEE, 2017, October,pp. 1–9. [5] S.Y. Huang, C.C. Lin, A.A. Chiu, D.C. Yen, Fraud detection using fraud triangle risk factors, Inf. Syst. Front 19 (6) (2017) 1343–1356. [6] A. Chouiekh, E.H.I.E. Haj, Convnets for fraud detection analysis, Proc. Comput. Sci. 127 (2018) 133–138. [7] A. Dal Pozzolo, G. Boracchi, O. Caelen, C. Alippi, G. Bontempi, Credit card fraud detection: a realistic modeling and a novel learning strategy, IEEE Transact. Neural Networks Learn. Syst. 29 (8) (2017) 3784–3797. [8] B. Baesens, V. Van Vlasselaer, W. Verbeke, Fraud Analytics Using Descriptive, Predictive, and Social Network Techniques: a Guide to Data Science for Fraud Detection, John Wiley & Sons, 2015. [9] A.C. Bahnsen, D. Aouada, A. Stojanovic, B. Ottersten, Feature engineering strategies for credit card fraud detection, Expert Syst. Appl. 51 (2016) 134–142. [10] T.F. Kummer, K. Singh, P. Best, The effectiveness of fraud detection instruments in not-for-profit organizations, Manag. Audit J. 30 (4) (2015) 435–455. [11] S.K. Majhi, Fuzzy clustering algorithm based on modified whale optimization algorithm for automobile insurance fraud detection, Evolutionary Intelligence 14(2021) 35–46. [12] D. Cheng, S. Xiang, C. Shang, Y. Zhang, F. Yang, L. Zhang, Spatio-temporal attention-based neural network for credit card fraud detection, in Proceedings of the AAAI Conference on Artificial Intelligence vol. 34, 2020, April, pp. 362–369, 1. [13] A. Zakaryazad, E. Duman, A profit-driven Artificial Neural Network (ANN) with applications to fraud detection and direct marketing, Neurocomputing 175 (2016) 121–131. [14] A.S. Bekirev, V.V. Klimov, M.V. Kuzin, B.A. Shchukin, Payment card fraud detection using neural network committee and clustering, Opt. Mem. Neural Network. 24 (3) (2015) 193–200. [15] S. Georgieva, M. Markova, V. Pavlov, Using the neural network for credit card fraud detection, in AIP Conference Proceedings vol. 2159, AIP Publishing LLC, 2019,October, 030013, 1.
Copyright
Copyright © 2024 Utkarsha Kulkarni , Rahul Paikrao. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET65243
Publish Date : 2024-11-14
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

